This is a global configuration mode command. Command Function Shell Function.

What Is Access Control List Acl Types Linux Vs Windows Imperva
An ACL is the same as a Stateless Firewall which only restricts blocks or allows the packets that are flowing from source to destination.
. What two functions describe uses of an access control list. Choose two ACLs assist the router in determining the best path to a destination. Access control lists are used for controlling permissions to a computer system or computer network.
Which two statements describe the effect of the access control list wildcard mask 00015. Access control list ACL refers to the permissions attached to an object that specify which users are granted access to that object and the operations it is allowed to perform. What two functions describe uses of an access control list.
Array Function Filter Function Join Function LBound Function Split Function UBound Function. There are two types of ACLs. C ACLs provide a basic level of security for network access.
- It is a numerical argument. Users may have one or more roles and may be assigned one or more permissions as a result. Click to see full answer.
TCO 6 What function describes the use of an access control list. Each entry in an access control list specifies the subject and an associated operation that is permitted. In short this list includes all of the information.
Asc Function Chr Function EuroConvert Function FormatCurrency Function FormatDateTime Function. While it is important for employees to be able to access the data they need it is sometimes even more crucial that a company protects its data from outside individuals. ACLs assist the router in determining the best path to a destination.
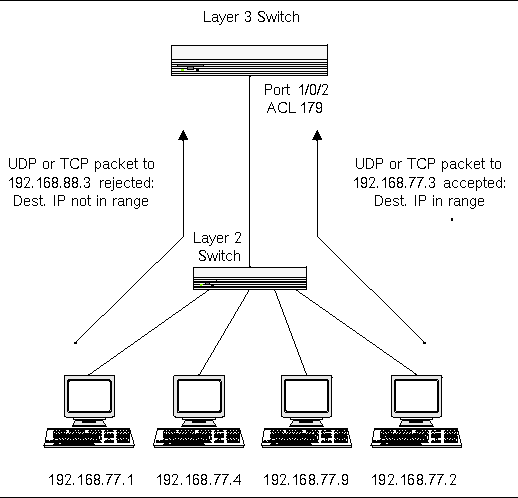
ACLs can control which areas a host can access on a network. The access-list command. Networking ACLs filter access to the network.
Program to calculate the Round Trip Time RTT Introduction of MAC Address in Computer Network Collision Avoidance in wireless networks Maximum Data Rate channel capacity for Noiseless and Noisy channels Types of switches in Computer Network Network. Choose two ACLs assist the router in determining the best path to a destination. An access control list ACL contains rules that grant or deny access to certain digital environments.
True True or False. They are used to filter traffic in and out of a specific device. Program to remotely Power On a PC over the internet using the Wake-on-LAN protocol.
This command uses the following syntax. Choose two a ACLs assist the router in determining the best path to a destination. Advertisement Techopedia Explains Access Control List ACL.
ACLs provide a basic level of security for network access. This topic for the IT professional describes access control in Windows which is the process of authorizing users groups and computers to access objects on the network or computer. ACLs provide a basic level of security for network access.
Filesystem ACLs filter access to files andor directories. ACLs provide a basic level of security for network access. ACLs work on a set of rules that define how to forward or block a packet at the routers interface.
The last four bits of a supplied IP address will be ignored. What two functions describe uses of an access control list. Choose two ACLs can control which areas a host can access on a network.
Standard ACLs can restrict access to specific applications and ports. Choose two ACLs assist the router in determining the best path to a destination. ACLs provide a basic level of security for network access.
What two functions describe uses of an access control list. Standard ACLs can restrict access to specific applications and ports. Key concepts that make up access control are permissions ownership of objects inheritance of permissions user rights and object auditing.
ACLs provide a basic level of security for network access ACLs can permit or deny traffic based upon the MAC address originating on the router. An access control list can control rights and privileges to anything from a network device to file storage systems and everything in between. Access Control Entries ACE A sequential list of permit or deny statements.
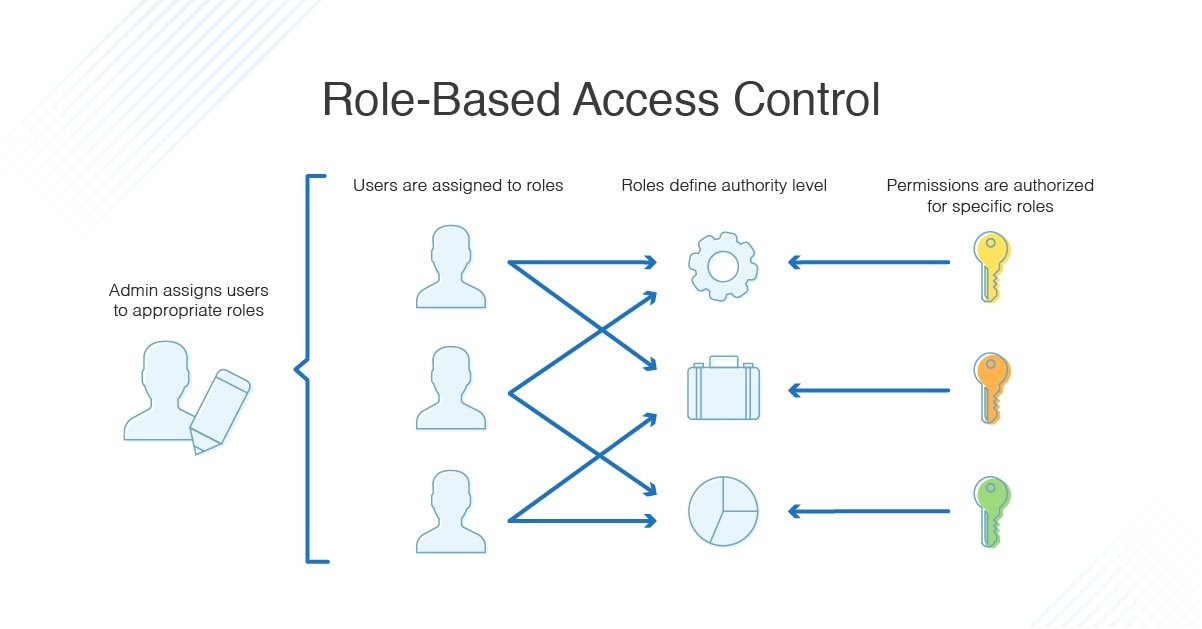
What function describes the use of an access control list. Role-Based Access Control RBAC As you can probably guess from the name role-based access control gives access permissions based on user roles. Access Control Lists ACLs are network traffic filters that can control incoming or outgoing traffic.
One of the most important functions of access control lists is the ability to prevent unauthorized users from accessing sensitive services or information. A router compares information within a packet against each ACE in sequential order to determine if the packet matches one of the ACEs. It is always preferred to use Extended ACLs since they are more.
Windows Server 2016. Standard ACLs can restrict access to specific applications and ports. ACLs provide a basic level of security for network access.
ACLs are a network filter utilized by routers and some switches to permit and restrict data flows into and out of network interfaces. Choose two The first 28 bits of a supplied IP address will be matched. ACLs ensure that routers avoid suboptimal paths.
View full document ACLs What two functions describe uses of an access control list. None of the above Type. Standard ACLs can restrict access to specific applications and ports.
ACLs can permit or deny traffic based upon the MAC address originating on the router. ACLs control which user can access what services on the Internet. Standard ACLs can restrict access to specific applications and ports.
ACLs can permit or deny traffic based upon the MAC address originating on the router. Choose two ACLs assist the router in determining the best path to a destination. Router config access-list ACL_ permitdeny conditions.
Choose two ACLs assist the router in determining the best path to a destination. Standard ACLs can restrict access to specific applications and ports. When an ACL is configured on an interface the network device analyzes data passing through the interface compares it to the criteria described in the ACL and either permits the data to flow or prohibits it.
What I mean by role is the functions that an employee performs. Filesystem ACLs tell operating systems which users can access the system and what privileges the users are allowed. ACLs can permit or deny traffic based upon the MAC address originating on the router.
This command allows us to create a standard-numbered ACL and an extended-numbered ACL. B Standard ACLs can restrict access to specific applications and ports. ACLs assist the router in.
ACLs can control which areas a host can access on a network. What are two uses of an access control list. ACLs provide a basic level of security for network access.
ACL statements What are Access Control Entries commonly called. Those devices can be network devices that act as network gateways or endpoint devices that users access directly. CreateObject Function GetObject Function.
Standard ACLs can restrict access to specific applications and ports.

Rbac Vs Abac Access Control What S The Difference Dnsstuff
0 Comments